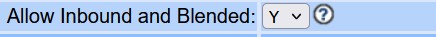
Vicidial 11 is installed on openSUSE Leap 15 .
Let’s go step-by-step to install WireGuard on openSUSE Leap 15, openSUSE uses zypper .
🧩 Step 1: Update your system
Run this first:
sudo zypper refresh
sudo zypper update -y
⚙️ Step 2: Install WireGuard package
WireGuard is included in the Kernel:HEAD or official repositories from Leap 15.2+.
Try installing directly:
sudo zypper install wireguard-tools
If you get an error (package not found), add the correct repository:
For openSUSE Leap 15.x:
sudo zypper addrepo https://download.opensuse.org/repositories/network:utilities/openSUSE_Leap_15.5/network:utilities.repo
sudo zypper refresh
sudo zypper install wireguard-tools
(Replace 15.5 with your actual version if needed — check with cat /etc/os-release.)
🔑 Step 3: Generate WireGuard keys
sudo mkdir -p /etc/wireguard
cd /etc/wireguard
sudo umask 077
sudo wg genkey | tee privatekey | wg pubkey > publickey
🧾 Step 4: Create the WireGuard configuration file
Create /etc/wireguard/wg0.conf:
sudo nano /etc/wireguard/wg0.conf
Add the following (example for server):
[Interface]
Address = 10.10.20.1/24
ListenPort = 51820
PrivateKey = <server-private-key>
# NAT rules (optional for internet routing)
PostUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
Replace:
eth0 with your WAN interface (ip a will show it)<server-private-key> with content from /etc/wireguard/privatekey
👥 Step 5: Add a peer (client)
Add this block to wg0.conf for each client:
[Peer]
PublicKey = <client-public-key>
AllowedIPs = 10.10.20.2/32
📡 Step 6: Enable IP forwarding
Enable forwarding permanently:
sudo sysctl -w net.ipv4.ip_forward=1
echo "net.ipv4.ip_forward = 1" | sudo tee -a /etc/sysctl.conf
🔥 Step 7: Allow WireGuard in firewall
For firewalld (default in openSUSE):
sudo firewall-cmd --permanent --add-port=51820/udp
sudo firewall-cmd --reload
For SuSEfirewall2 (older versions):
sudo yast firewall
→ Add UDP port 51820 under “Allowed Services”.
🚀 Step 8: Start and enable WireGuard
sudo systemctl enable wg-quick@wg0
sudo systemctl start wg-quick@wg0
Check status:
sudo systemctl status wg-quick@wg0
✅ Step 9: Verify connection
Run:
sudo wg
You’ll see your interface and peers.
💡 Optional: Client example
Example client /etc/wireguard/wg0.conf:
[Interface]
Address = 10.10.20.2/24
PrivateKey = <client-private-key>
[Peer]
PublicKey = <server-public-key>
Endpoint = <server-public-ip>:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25
Working Example as Vicidial as client
[Interface]
PrivateKey = KLqd0EmF48k8ij44UZnFUnABGGpoIqINDcjN+3Zs4XU=
Address = 10.34.203.3/32
[Peer]
PublicKey = WV+3XLuwHoRe4ivRiBoC8d2UjVqQSnfW53PCA9k0=
AllowedIPs = 10.34.203.0/24, 172.16.60.0/24
Endpoint = 11.11.11.11:13231
Then start on the client:
sudo wg-quick up wg0
start on reboot
crontab -e
@reboot /etc/wireguard/wg0.conf
@reboot /etc/wireguard/keepalive.sh
vicibox11:~ # cat /etc/wireguard/keepalive.sh
#!/bin/bash
TARGET="10.34.202.1" # replace with your WireGuard peer IP
while true; do
ping -c 10 $TARGET
sleep 60
done
✅ Done!
WireGuard is now running on your openSUSE Leap 15 VICIdial server.